In an age where the digital realm offers both unparalleled opportunities and lurking dangers, how can we navigate the complex landscape of online content and maintain both our privacy and our ethical boundaries? The proliferation of deepfakes, the evolution of digital marketing strategies, and the increasing accessibility of technologies like "deephot link" demand that we approach the internet with a critical eye and a firm grasp of the tools at our disposal.
The echoes of a bygone era still resonate, whispering of a time when glossy pages and carefully curated imagery shaped our understanding of beauty and desire. "Goodbye to adult magazine cutouts, its been a good run with playboy magazine and the era of sticky pages," a sentiment often expressed as we transition into an era dominated by digital renderings and the potential for manipulation. It is imperative to remember that these technological marvels, while impressive, also open doors to the exploitation of individuals and the spread of misinformation. We must approach this brave new world with caution.
The rise of technologies like deepfakes serves as a stark reminder of the need for vigilance. "These deepfake nudes are so good they look like they were taken by the celebrity themselves," the technology is capable of blurring the lines between reality and illusion. This capability has far-reaching implications, from the potential for malicious impersonation to the erosion of trust in visual media. The potential for misuse is significant, and it is vital that we understand the technologies, so that we may be aware of them.
Consider the following table, which outlines some of the dangers inherent in the misuse of deepfake technologies. We must understand these in order to defend ourselves and others from harm:
| Potential Misuse | Consequences |
|---|---|
| Impersonation and Identity Theft | Financial fraud, reputational damage, emotional distress |
| Spread of Misinformation and Propaganda | Erosion of trust in institutions, manipulation of public opinion, social unrest |
| Non-Consensual Intimate Imagery | Emotional trauma, legal ramifications, damage to personal relationships |
| Blackmail and Extortion | Financial loss, psychological manipulation, safety concerns |
We can ask the question: "How about instead of spying on your sister in the shower, you enter the pics from her beach vacation into deep nude and jerk off to her naked body without the risk of arrest or embarrassment?" This raises unsettling questions about the ethics of our curiosity and the consequences of crossing personal boundaries. It underscores the importance of critical thinking. "Whatever keeps you from sniffing your sister's panties," is not a solution; it's an echo of the problem.
This brings us to the core concepts we're exploring: "Explore the world of deephot link and uncover its powerful potential. Discover how this innovative technology enhances photography, offering an immersive visual experience." "Deephot.link is an innovative online platform designed to help artists, photographers, and content creators showcase their work in a visually appealing manner. Deephot.link isn't just another platform; It's a gateway to a world of possibilities. By providing safe and efficient access to the deep web, it empowers users to explore, learn, and grow in ways they never thought possible." In a world where digital content reigns supreme, understanding how to effectively showcase and disseminate your work is paramount. Yet, we must always be aware of the potential for this technology to be misused, and be prepared for this eventuality.
Lets examine the possibilities in a more structured format. The table below details the potential advantages and disadvantages associated with using "deephot link" and similar platforms. This information is for education and exploration.
| Potential Advantages | Potential Disadvantages |
|---|---|
| Enhanced Visual Experience: Immersive and engaging presentation of visual content. | Privacy Concerns: Potential for unauthorized use or exposure of sensitive data if security measures are inadequate. |
| Increased Engagement: Greater interaction and connection with viewers through advanced features. | Security Risks: Susceptibility to hacking, malware, or other cyber threats if the platform is not secure. |
| New Creative Dimensions: Opportunities for artists and photographers to experiment with innovative presentation techniques. | Ethical Considerations: Potential for misuse, such as the creation of misleading content or the exploitation of individuals. |
| Wider Reach: Increased visibility and exposure for creators, leading to broader audiences and enhanced influence. | Reliance on Technology: Dependence on technology and potential for technical glitches or malfunctions. |
Consider the impact of "In an era where data privacy is a growing concern, this tool offers a unique solution that combines ease of use with robust security features." The promise of secure and efficient access is crucial in this age of relentless digital surveillance. We must always ensure that any technology we utilize, particularly one that interfaces with the internet, is doing everything possible to protect user data.
"Connect to any computer at any time. Smooth enough to play games, free for personal use!" the appeal of remote access technology is undeniable. From a practical perspective, it allows us to work, play, and communicate from anywhere in the world. The caveat, however, is that it demands an abundance of caution. This is especially important with security and it is something that must be considered.
The evolution of the digital landscape has given rise to new strategies for success. "In the vast landscape of digital marketing, the term deep hot link has emerged as a crucial concept for website optimization and user engagement. Web site owners who do not want search engines to deep link, or want them only to index specific pages can request so using the robots exclusion standard (robots.txt file). In the vast landscape of digital marketing, the term deep hot link has emerged as a crucial concept for website optimization and user engagement. Web site owners who do not want search engines to deep link, or want them only to index specific pages can request so using the robots exclusion standard (robots.txt file)."
This brings us to the mechanics of implementation. Here are "12 powerful deephot link strategies," which "Unleash your website's potential. Discover effective techniques to enhance your online presence, boost traffic, and achieve higher rankings. Learn how to create compelling content, build authority, and leverage the power of backlinks for a successful digital presence."
| Deep Hot Link Strategy | Description |
|---|---|
| 1. Keyword Optimization | Select relevant keywords and incorporate them strategically throughout your content, including headers, titles, and body text. |
| 2. Compelling Content Creation | Produce high-quality, informative, and engaging content that provides value to your audience and encourages them to link to your website. |
| 3. Backlink Building | Acquire backlinks from reputable websites in your industry to increase your website's authority and improve search engine rankings. |
| 4. Internal Linking | Link to relevant pages within your own website to improve user experience, increase time on site, and distribute link juice. |
| 5. Guest Blogging | Write guest posts for other websites in your niche and include links back to your website to increase exposure and attract new visitors. |
| 6. Broken Link Building | Find broken links on other websites and offer to replace them with links to your relevant content, providing value and acquiring backlinks. |
| 7. Resource Page Creation | Create a dedicated resource page on your website that lists valuable resources, including links to other websites, and promotes your own content. |
| 8. Infographic Creation and Promotion | Design visually appealing infographics that present data or information in an engaging way and share them on social media and other platforms. |
| 9. Social Media Promotion | Share your content on social media platforms to increase visibility, drive traffic, and encourage sharing and linking. |
| 10. Email Outreach | Reach out to bloggers, journalists, and influencers in your industry and share your content with them, requesting backlinks or mentions. |
| 11. Competitor Analysis | Analyze your competitors' backlink profiles to identify opportunities to acquire similar backlinks and improve your own website's authority. |
| 12. Local SEO Optimization | Optimize your website for local search by including local keywords, creating a Google My Business profile, and acquiring local citations. |
The building blocks of a link must be thoroughly understood. "This link is made up of: The authority and hostname, in." the creation and proper use of URLs, the fundamental components of online communication, is crucial to success. You must never overlook the basic concepts.
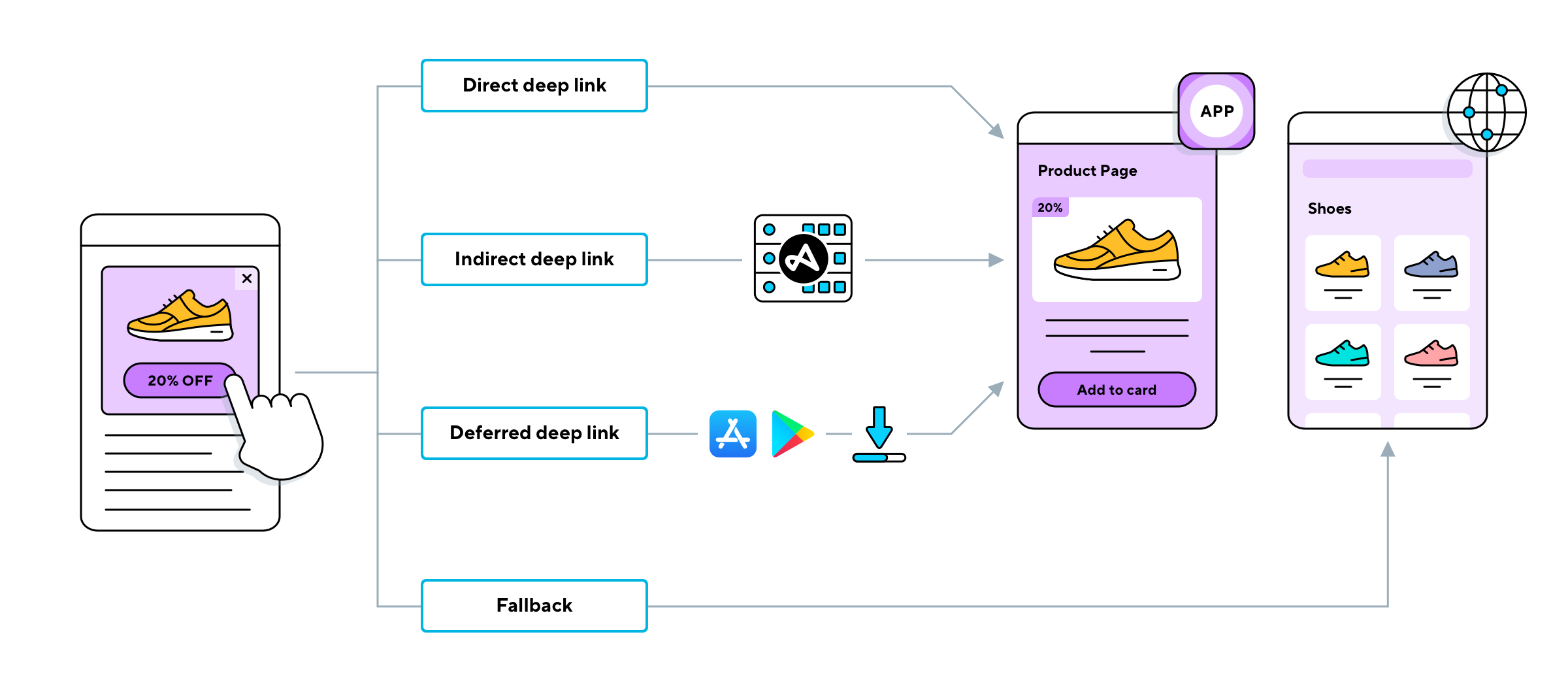
A clear understanding of the structure of a URL is essential for the proper utilization of deep linking techniques. Here's how to deep link a URL and why it is used: "Here is how you can deep link a url: Set a particular goal for your business campaign. Tweak the objectives of your campaign according to its significance for buyers. provide seamless user experience with deep links. Using deep links can help you to provide the best possible user experience to your visitors. Deep links are a fundamental feature in the arsenal of mobile marketers and app developers alike. They serve as the critical connectors between users and specific content or actions within mobile apps and websites."
The purpose of using deep links is to provide users with an intuitive and frictionless experience when navigating apps and websites. When used correctly, deep links can create a streamlined flow between content and the user.